In today’s digital landscape, data security and compliance are more critical than ever. For organizations using Salesforce, ensuring that all user activities are properly monitored and documented is a significant challenge. Unauthorized access, data breaches, and inadvertent errors can lead to serious vulnerabilities if not detected early. This is where Change Intelligence comes into play. In this blog, you will learn about Change Intelligence, a key feature of OpsBridge, developed by CloudFulcrum. OpsBridge is a sophisticated release orchestration suite designed to transform Salesforce DevOps, offering a comprehensive range of capabilities that go beyond traditional DevOps tools.
What is Change Intelligence?
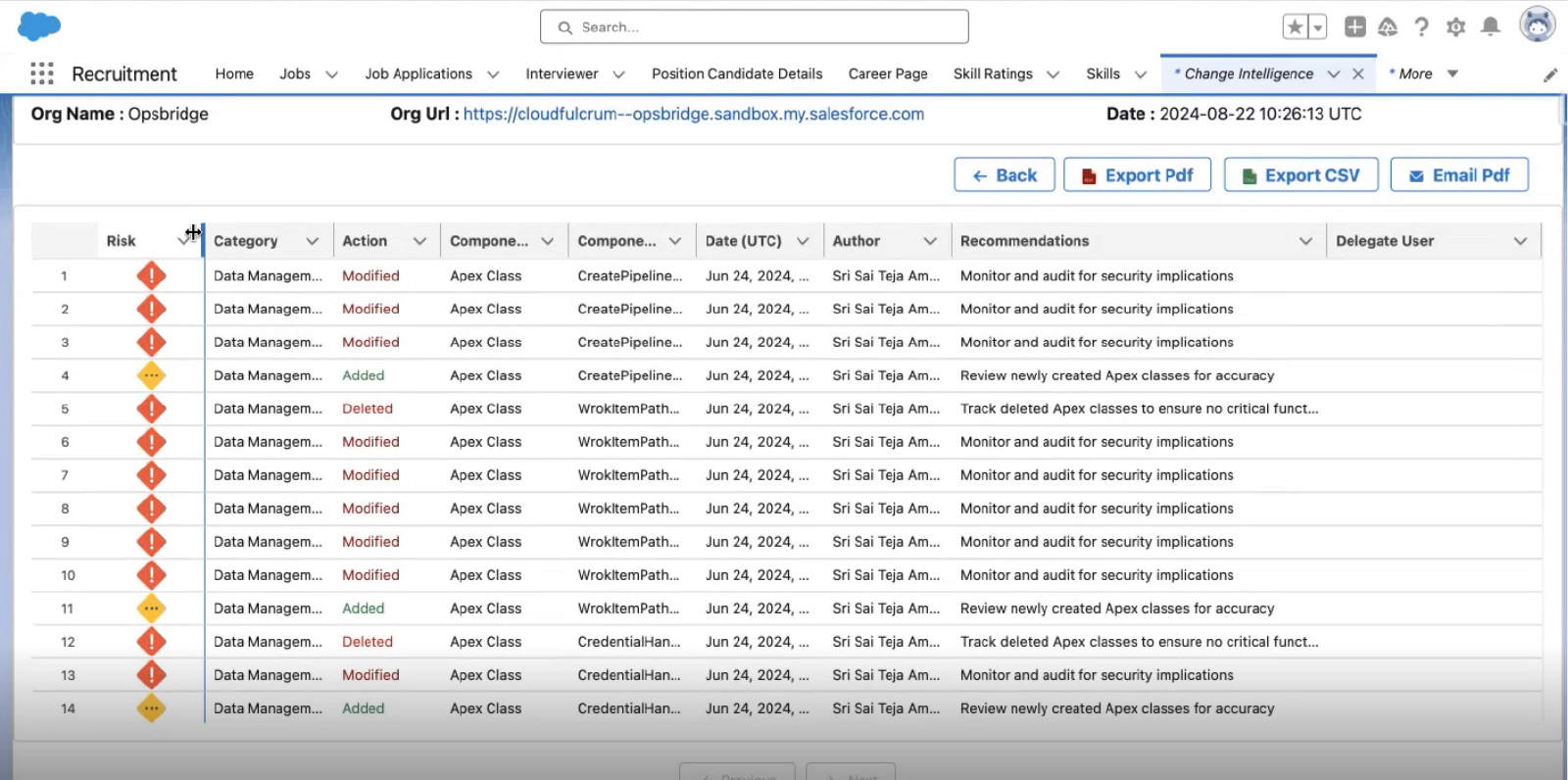
Change Intelligence is detailed records that track user activities within the platform. These logs capture everything from user logins and data access to changes made to records and system configurations. Essentially, they provide a comprehensive overview of who did what, when, which component type, which component, what is the Change Risk and what is the change group from where within the Salesforce environment.
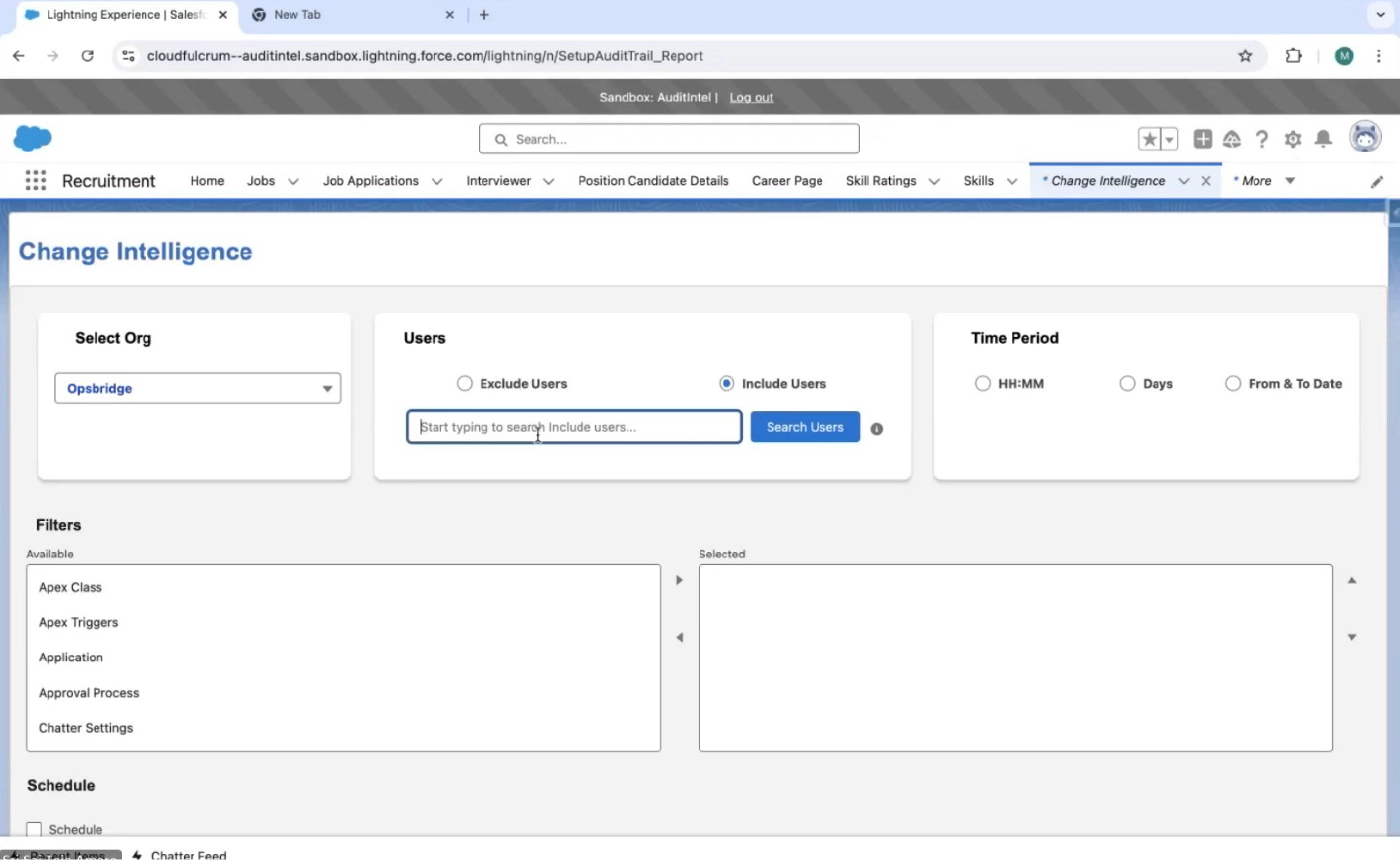
The Importance of Change Intelligence
Change Intelligence are more than just a record-keeping tool; they are vital for several key reasons:
User Activity Monitoring
- Tracking Logins and Logouts: To track user logins and logouts, recording details like IP addresses and timestamps. This helps ensure that only authorized personnel are accessing the system.
- Monitoring Data Access: Logs show which users accessed or modified specific records, ensuring accountability and transparency in data handling.
Security and Compliance
- Identifying Unauthorized Access: By having Change Intelligence, organizations can quickly identify and respond to suspicious activities, such as unauthorized access attempts or unusual data access patterns.
- Compliance Reporting: Many industries have strict regulatory requirements for data handling. It provide the necessary documentation to demonstrate compliance with these regulations.
Change Segmentation
- By segmentation changes into Administration, Customization, Security, and other key areas, you can efficiently monitor user activities and maintain system integrity.
Risk Score
- Identify and add risk scores to changes based on their potential impact. For example, changes made by users with high-level permissions or modifications to critical system settings might receive higher risk scores. This scoring system allows organizations to prioritize their review and response efforts, focusing on the most critical changes first.
Storage for Extended Periods
- This ensures compliance with long-term data retention policies and provides historical data for audits and investigations.
Troubleshooting and Forensics
- Investigating Issues: When issues like data corruption or unexpected changes occur, this help trace the problem back to its source, enabling quicker resolution.
- Forensic Analysis: In the event of a security breach, this can be used to reconstruct the sequence of events, providing critical information for forensic investigations.
Change Management
- Tracking Configuration Changes: This monitor changes to Salesforce settings, such as user permissions and role hierarchies, ensuring that all changes are authorized and properly implemented.
- Monitoring Deployment Activities: These logs help track deployment activities, ensuring that system changes are correctly managed and do not introduce new vulnerabilities.
Performance Monitoring
- Identifying Performance Bottlenecks: By analysing patterns in system usage, this can help identify times of high activity or users who may be overloading the system, aiding in performance optimization.
- Optimizing Resource Allocation: Understanding user interaction with Salesforce can help in optimizing resources, such as server capacity and user licensing.
Legal and Internal Investigations
- Supporting Legal Cases: In legal disputes or investigations, this provide documented evidence of user actions, which can be critical in court.
- Internal Audits: Organizations can use this to conduct internal audits, ensuring adherence to company policies and identifying areas for improvement.
Advanced Security Measures
- AI-powered Fraud Detection and Alerting: Leveraging artificial intelligence, organizations can detect and respond to fraudulent activities in real-time. AI can analyse patterns and behaviours in changes, alerting administrators to potential threats before they escalate into major issues.
Best Practices for Leveraging Change Intelligence
To maximize the benefits of Change Intelligence, consider the following best practices:
- Regular Monitoring: Set up a routine to review changes regularly. This proactive approach helps in early detection of issues.
- Automated Alerts: Use automated alerts to notify administrators of suspicious activities, such as repeated failed login attempts or unauthorized data access.
- Data Retention Policies: Establish clear data retention policies for changes to ensure that historical data is available when needed but does not clutter your system unnecessarily.
- Compliance Integration: Ensure that your audit trail processes are integrated with your compliance frameworks, making it easier to demonstrate adherence to regulatory requirements.
- User Education: Educate users on the importance of change and how their activities are monitored. This can foster a culture of accountability and security awareness.
Conclusion
Change Intelligence plays a crucial role in safeguarding the integrity, security, and compliance of Salesforce environments. By meticulously tracking user activities, changes, and system interactions, organizations can effectively monitor and manage their platforms, minimizing risks associated with unauthorized access, data breaches, and inadvertent errors.

